Is an Alternative Term Used to Describe Asymmetric Cryptographic Algorithms
Private key cryptography d. What alternative term can be used to describe asymmetric cryptographic algorithms.
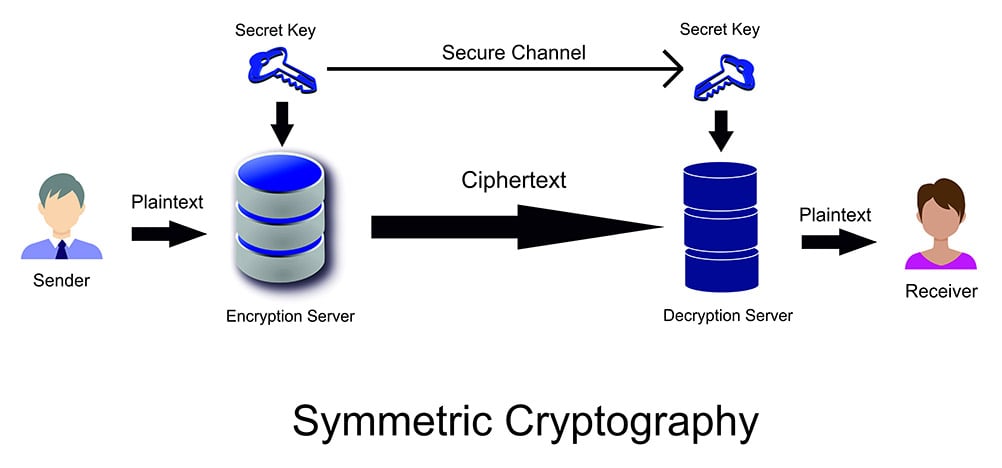
Symmetric Vs Asymmetric Encryption What S The Difference
Asked Feb 15 2019 in Computer Science Information Technology by SuperMario networking-and-telecommunications.

. Moreover asymmetric cryptography requires higher processing and long keys at least 1024 bits for RSA 31 to be used. Public-key cryptography requires the significant effort of deploying a PKI. User key cryptography B.
A user key cryptography. What alternative term can be used to describe asymmetric cryptographic algorithms. What alternative term can be used to describe asymmetric cryptographic algorithms answer choices.
Select the secure alternative to the telnet protocol. Three Main Types of Cryptographic Algorithms There are three main types of cryptographic algorithms. Choose all that apply Answer.
Select the term used to describe tracking software that is deployed without the consent or control of the user. C public key eryptography. What altemative term can be used to describe asymmetric cryptographic al algorithms.
Public key cryptography 6. Electrical Engineering questions and answers. Asymmetric cryptographic algorithms are also known as private key cryptography.
Public key cryptography c. It is pair of algorithms that take a key and convert plaintext to ciphertext andback. User key cryptography b.
True Wireless data networks are particularly susceptible to known ciphertext attacks. The algorithm was introduced in the year 1978. As implied by the key names the public key used to encode plaintext can be made available to anyone.
User key cryptography b. Wireless data networks are particularly susceptible to known ciphertext attacks. User key cryptography e.
What alternative term can be used to describe asymmetric cryptographic algorithms. It is a science that applies complexmathematics and logic to design strong encryptionmethods. RSA is a first successful public key cryptographic algorithmIt is also known as an asymmetric cryptographic algorithm because two different keys are used for encryption and decryption.
It is also called as private key cryptography. One alternative term for asymmetric cryptographic algorithms is public-key cryptography. Public-key algorithm An asymmetric cipher that uses two keys one for encryption the public key and the other for decryption the private key.
A set of cryptographic keys used for public-key cryptography. Public key cryptography c. Private key cryptography D.
1 secret key 2 public key and 3 hash functions. RSA is named after Rivest Shamir and Adleman the three inventors of RSA algorithm. Asymmetric cryptographic algorithms are mathematical functions used to encrypt data in a way so that decryption can only be achieved by someone having knowledge of what key was used to encrypt it.
If Alice has a message to send to Bob and she wants to encrypt the message using asymmetric cryptography so that no one other than Bob can read it she does so by using Bobs public key. Asymmetric cryptographic algorithms are also known as private key cryptography. False Wireless data networks are particularly susceptible to known ciphertext attacks.
This new algorithm sought to solve its predecessors main weakness a short encryption key length vulnerable to brute force. B private key cryptography. What alternative term can be used to describe asymmetric cryptographic algorithms.
Which of the following are considered to be common asymmetric cryptographic algorithms. Pick an algorithm for any one of these types eg DES AES RSA MD5 and describe how it works and where it is applied For example SSL uses 3DES or DES for message encryption. What alternative term can be used to describe asymmetric cryptographic algorithms.
It is a value that is known to the sender. - user key cryptography - public key cryptography - private key cryptography - cipher-test cryptography. Asymmetric cryptographic algorithms are also known as private key cryptography.
However because of these. Alternative public-key cryptographic schemes such as ECC 32 might require shorter keys to be used in order to achieve the same security than RSA keys. Private key cryptography d.
AES is one of the most common symmetric encryption algorithms used today developed as a replacement to the outdated DES Data Encryption Standard cracked by security researchers back in 2005. Asymmetric cryptographic algorithms are also known as private key cryptography. What alternative term can be used to describe asymmetric cryptographic algorithms.
Private key cryptography d. What alternative term can be used to describe asymmetric cryptographic algorithms. Public key cryptography C.

Asymmetric Cryptography An Overview Sciencedirect Topics

Types Of Encryption 5 Encryption Algorithms How To Choose The Right One Security Boulevard

No comments for "Is an Alternative Term Used to Describe Asymmetric Cryptographic Algorithms"
Post a Comment